Understanding the cyber threat landscape
This is the second in a series of blog posts from our Information Security Lead Marise Alphonso, where she talks about some of the information security issues facing the not-for-profit sector.
Years ago we had to contend with the likes of script kiddies breaking through the organisational network perimeter by creating malware for fun. Those were the days when the firewall was the perimeter and the word “cloud” referenced the fluffy white or dark grey matter in the skies above us.
Technology has since evolved dramatically with the widespread use of the internet, social media channels, cloud services, increasing uptake of smart devices and Internet of Things (IoT) devices and the proliferation of ways of creating and consuming data.
The fast-changing pace of technology coupled with a mobile workforce and device use outside of organisational controls means that cyber threat actors currently have a much wider attack surface at their disposal to target the general public, organisations and governments worldwide.
To 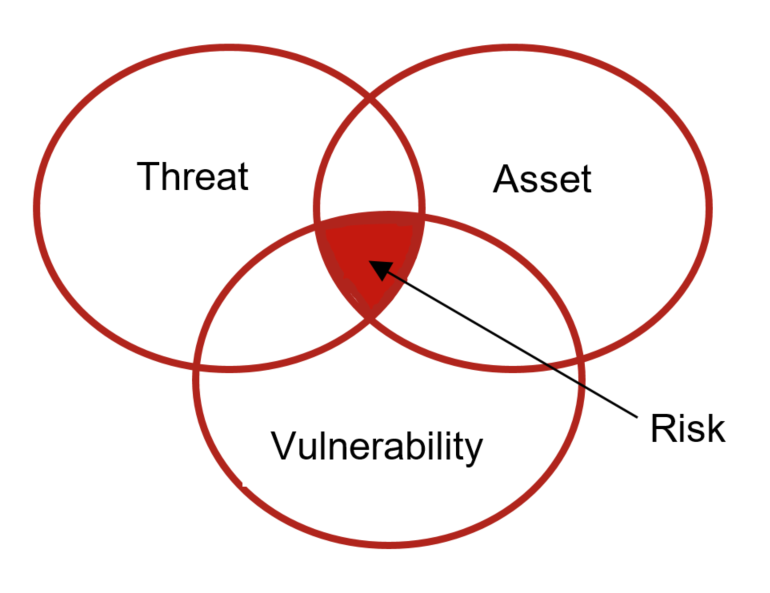 effectively address these threats, the cyber risk discussion must be channelled from IT to the business to facilitate decision-making on how risk reduction activities could reduce the organisational threat surface and close vulnerability gaps while protecting assets, meeting regulations, compliance obligations and business needs.
effectively address these threats, the cyber risk discussion must be channelled from IT to the business to facilitate decision-making on how risk reduction activities could reduce the organisational threat surface and close vulnerability gaps while protecting assets, meeting regulations, compliance obligations and business needs.
There has often been thought patterns that a particular industry or organisation would never be targeted by cyber attackers. The fact of the matter is that organisations of any size and in any industry are subject to attacks. Types of cyber attack groups are listed below:
Type |
Motives |
|
Accidental or malicious insiders |
Accidents by internal staff can happen and could lead to adverse events for organisations. Malicious insiders could have various motives ranging from theft of Intellectual property to corporate espionage |
|
Hacktivists |
Keen on advancing a political or social change agenda or expose wrongdoing |
|
Cyber criminals |
Intent on financial gain |
|
Third party |
Connectivity and interdependence via the supply chain could facilitate unintended compromise |
|
Nation states |
Nationalism and intent on gaining secrets and disrupting other nations |
|
Cyber Terrorists |
Religious and political beliefs; attempt to disrupt critical infrastructure |
|
Script Kiddies |
Intent on self-fame and make use of existing tools and techniques to do so |
The manifestation of cyber threats results in incidents or data breaches; where incidents are defined as security events that compromise the confidentiality, integrity or availability of information and data breaches result in confirmed disclosure of data to an unauthorised party.
This distinction in definition drawn from the Verizon Data Breach Investigations Report 2019 shows data that indicates incidents occur mostly due to Denial of Service attacks, or lost or misplaced devices/information whereas data breaches occur mostly due to phishing or the use of stolen credentials.
The meaningful point made is that the primary web application attack vector was the front-end to cloud-based email servers, presenting users with fake log-in pages to web-based email. This is re-stated by Cisco in their 2019 threat report where email is stated as the most common threat vector.
Hence, focusing organisation efforts on training employees in recognising phishing emails and the use of multi-factor authentication will be a useful exercise to aid in preventing the success of these types of attacks.
Some of the current attack trends include “Flight to ease” and “Business Email Compromise”, where the latter refers to increased phishing targeting senior management. Both trends highlight the focus on the easiest path to exploitation – “Flight to ease” refers to the extent with which criminals switch to the next easiest thing to exploit or attack, as is the targeting of senior management which could be the most simplistic path to financial gain.
Threat trends are shown in the image below, where crypto jacking was flagged as new last year potentially due to increases in the value of cryptocurrency.
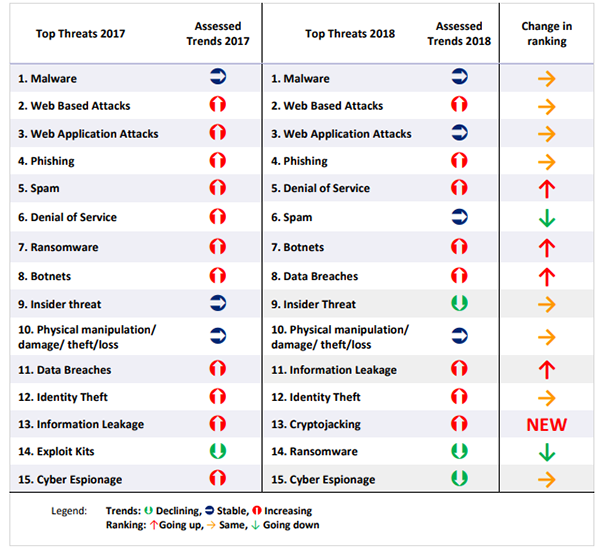
Source: European Union Agency for Network and Information Security (ENISA), ENISA Threat Landscape Report 2018, January 2019, pg. 115
Recent statistics from the ABS indicate that one in 10 Australian businesses suffered a data breach or security incident in the last year.
With the Notifiable Data Breach scheme effective from February 2018 there is certainly a heightened awareness of the need for improved security and data protection practices.