Why not-for-profits need to stay informed on the latest information security threats
The year 2020 has been a challenge for all of us and the way we work. In a year when organisations have had to adapt to many changes, the one constant in the information security arena is that security threats are always changing.
As a typical business would over time, adversaries adapt their operating models to determine how they can best grow their revenue. The market in this case? Primarily the demand for and supply of unprotected data. Data is after all, due to our ever-increasing digital presence, the new currency.
In a two week period of mid-late March 2020, as work and life routines began to shift in response to COVID-19, the Australian Cyber Security Centre (ACSC) received over 45 pandemic-themed security incident reports ranging from advice purporting to originate from the World Health Organisation to COVID-19 relief payment scams and working from home scams.
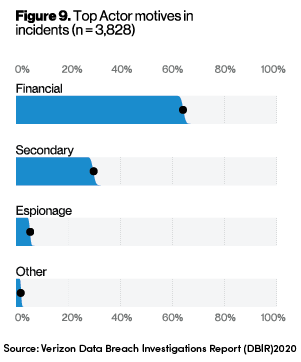 The Verizon Data Breach Investigations Report 2020 (DBIR), which provides global data-driven insights on over 32,000 information security incidents, highlights that the threat landscape is dominated by “financially-motivated” organised crime groups. The primary tactics or methods used to target individuals and organisations include phishing, the use of stolen usernames and passwords and the exploitation of errors made while configuring or maintaining IT systems. The ACSC annual cyber threat report echoes that the same techniques have been seen in Australia.
The Verizon Data Breach Investigations Report 2020 (DBIR), which provides global data-driven insights on over 32,000 information security incidents, highlights that the threat landscape is dominated by “financially-motivated” organised crime groups. The primary tactics or methods used to target individuals and organisations include phishing, the use of stolen usernames and passwords and the exploitation of errors made while configuring or maintaining IT systems. The ACSC annual cyber threat report echoes that the same techniques have been seen in Australia.
Phishing, which is a form of social engineering, has been in the bag of tactics used for a number of years due to the success of preying on human vulnerability and toying with emotion. The result has been the disclosure of sensitive personal information, passwords, bank details and more.
Organised crime groups have affiliate relationships, and as the ACSC report points out, form part of a supply chain offering cybercrime-as-a-service. Part of the offerings here could include ransomware, malicious software which when installed on your machine can extract your data and encrypt it, rendering it useless unless you pay a ransom.
When a security incident results in the disclosure of personal information, consideration must be made as to the obligations under the Notifiable Data Breaches scheme of the Privacy Act(1988). The link between security and data privacy was explored in a previous article.
Business email compromise (BEC) is another common attack, targeting businesses for financial gain. Generally involving requests for payment transfers or change of bank account details on supplier invoices or payroll, the intent is to redirect funds to bank accounts controlled by cybercriminals. This could be classed in the category of “secondary” motivations from the DBIR where targeted organisations or individuals are used as a means to an end by having their communications impersonated.
Some ways to protect yourself and your organisation against the common tactics, techniques and procedures used by cybercriminals include:
- Exercise caution when faced with unsolicited requests for personal information or a call to action requiring links to be clicked or attachments to be opened. These requests could be via SMS, phone calls, emails or instant messaging. If the message is from an organisation you may have dealings with, visit their website or phone them directly to engage in communication. Take this quiz to check if you can spot a phishing message.
- Secure your access. Use strong, unique passwords and multi-factor authentication (also known as two-factor authentication) on your accounts that hold sensitive information. The use of a password manager is highly recommended.
- Keep your software updated – this includes your operating systems, web browsers or any software you have installed on your machine. Software updates include new features and fixes to security vulnerabilities that are often found by security researchers.
- Back up your critical data – ensure you have a process in place for this.
- Have a robust process for verifying change of bank or account details requested by your suppliers and staff.
- Report any instances of security incidents to ReportCyber. This will give you access to assistance and advice and further protect the digital ecosystem.
Read more about how to protect your organisation's information security